BLE spam involves the unbidden sending of data packets to receptive Bluetooth devices within its vicinity. It is prevalent in crowded public locations like shopping centers, airports, and busy streets, where there is a high concentration of Bluetooth-enabled devices. Advertisers or malicious actors...
BLE spam involves the unbidden sending of data packets to receptive Bluetooth devices within its vicinity. It is prevalent in crowded public locations like shopping centers, airports, and busy streets, where there is a high concentration of Bluetooth-enabled devices. Advertisers or malicious actors utilize BLE to broadcast unwelcome messages or prompts, aiming to redirect users to targeted websites or advertisements.
Negative Effects of BLE Spam
Privacy Concerns: BLE spam can facilitate user tracking by repeatedly sending distinct identifiers to individuals, often unnoticed by the user, raising significant privacy issues.
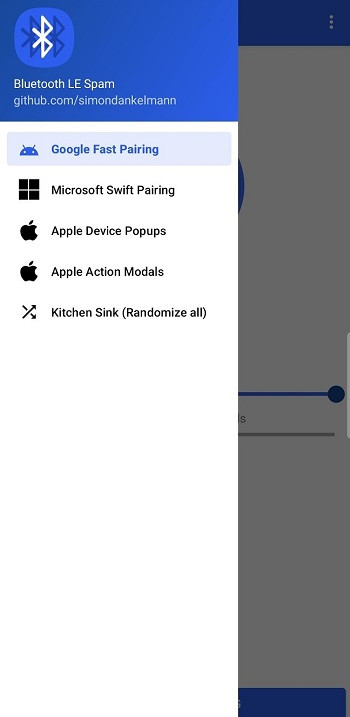 Privacy Risks of BLE Spam
Privacy Risks of BLE Spam
Security Threats: BLE spam can deliver malicious content, posing security challenges. Unintended acceptance of a harmful prompt could lead to device vulnerability.
User Frustration and Device Interruption: Frequent spam messages lead to user irritation. Additionally, these unsolicited disturbances can affect the normal performance of Bluetooth-enabled devices, resulting in a suboptimal user experience.
Strategies to Combat BLE Spam for Android Users
Enhancing User Awareness: Educating users about the dangers of accepting unknown Bluetooth connections is essential. Awareness initiatives can guide users on identifying and avoiding BLE spam effectively.
Device-Level Interventions: Manufacturers can implement features that allow users to block or filter BLE requests seamlessly. Features like auto-rejection of requests from unidentified devices could enhance user protection.
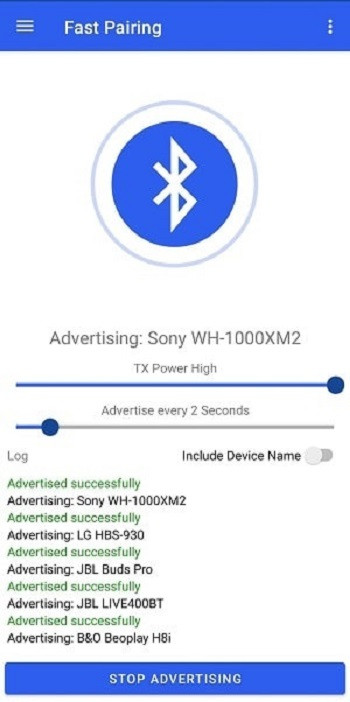 Security Solutions for BLE Spam
Security Solutions for BLE Spam
Regulatory Controls: Authorities can establish standards and regulations to curb BLE’s misuse for spamming, ensuring public safety.
Improved Security Protocols: Deploying sophisticated security protocols and encryption in BLE communications can mitigate the risk of receiving malicious spam.
Advancements in BLE and Future Spam Prevention
As Bluetooth technology progresses, strategies to address spam will evolve accordingly. Future versions of BLE promise more robust security measures, reducing unauthorized data transmission. Further, the use of AI and machine learning will likely enhance detection and prevention of BLE spam, maintaining a balance between BLE’s benefits and the necessity for enhanced security and privacy.
Final Thoughts
The challenges posed by BLE spam concerning privacy, security, and user satisfaction necessitate a collaborative effort among users, industry stakeholders, and regulators. Through advancements in Bluetooth technology towards more secure iterations, and collective vigilance, the impact of BLE spam can be significantly reduced, fostering a safer and more user-friendly digital environment.
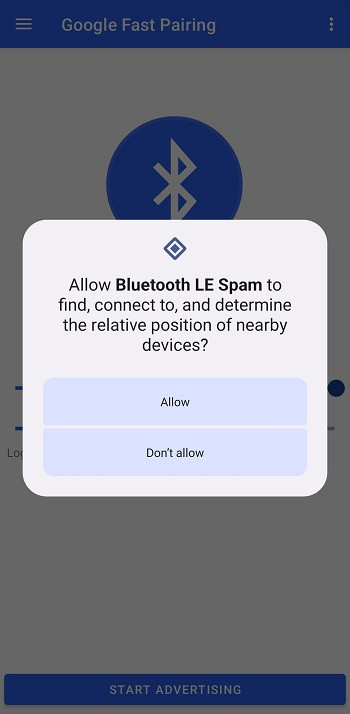 Concerns of Bluetooth LE Spam
Concerns of Bluetooth LE Spam
 Privacy Risks of BLE Spam
Privacy Risks of BLE Spam Security Solutions for BLE Spam
Security Solutions for BLE Spam